Here are some of the top marketing and communications jobs listed on FlexJobs. The computer can be used from the remote place if the suspects computer is connected to other computer or investigators computer using the network.
Computer Forensics Exam 1 Flashcards Quizlet
The ____ command creates a raw format file that most computer forensics analysis tools can read which makes it useful for data acquisitions.
. As you can see shutting a system down prior to acquisition could cause significant loss of evidence. Vodafone and Mannesmann merger 1999 - 2028B. Typically an ____ acquisition is done on a computer seized during a police raid for example.
AOL and Time Warner merger 2000 - 182B. The most common method to collect data. United States Department of Defense.
All of the above. Rule 2 Bet on Portfolio Performance. Most remote acquisitions have to be done as ____ acquisitions.
Here we discuss the top 4 types. This allows for adaptability by incident response analysts in the event that a tool or technique does not work. ACQ1010 Mod 3 Exam 07 Feb 2021pdf.
Creating a disk-to-image file. Antivirus antispyware and firewall porgrams. 10 ways to estimate operational synergies in MA deals are.
ACQ 101 Module 1 Testdocx. Gaz de France and Suez merger 2007 - 182B. You can learn more about financing from the following articles.
My second rule is to manage acquisitions as you would a portfolio of investments. To justify paying more than rival bidders the acquiring company needs to be able to do more with the acquisition than the other bidders in the MA process can ie generate more synergies MA Synergies MA Synergies occur when the value of a merged company is higher than the sum of the two individual companies. Access permission over the internet.
Online live real-time. A list of the biggest mergers and acquisitions. Ciscos growth strategy is based on identifying and driving market transitions.
Our acquisition strategy brings new technologies and business models to Cisco. For both types there are 4 methods of collecting data. Is the way to collect digital evidence when a computer is powered on and the suspect has been logged on to.
1 analyze headcount 2 look at ways to consolidate. Dow Chemical and DuPont merger 2015 - 130B. Online live real-time.
Horizontal Acquisition Vertical Acquisition Congeneric Acquisition Conglomerate Acquisition and examples. 10 ways to estimate. Remote Acquisition As the technology is developing the investigator doesnt need to go to the place of crime and capture the files from the suspect computer.
Remote Acquisition As the technology is developing the investigator doesnt need to go to the place of crime and capture the files from the suspect computer. This type is preferred when the hard disk is encrypted with a password. Many managers today regard buying a company for access to.
If damage occurs to the computer forensics lab it does not need to be repaired immediately. This is mostly done for diversification. The preferred method for the acquisition of memory is through direct contact with the suspect system.
Verizon and Vodafone acquisition 2013 - 130B. This article has been a guide to Types of Acquisition. Typically an ____ acquisition is done on a computer seized during a police raid for example.
Defense Security Cooperation Agency. Our first goal in digital forensics is to preserve evidence. Director of marketing campaigns.
If the computer has an encrypted drive a ____ acquisition is done if. Most remote acquisitions have to be done as ____ acquisitions. Up to 5 cash back Remote acquisition.
This method is also faster at obtaining the necessary files as it does not depend on a stable network connection. Examples of Bill of Sale. It is equally important to prove what is present as it is to prove what is not present.
That is rather than making one. The use of acquisitions to redirect and reshape corporate strategy has never been greater. Many attorneys like to have printouts of the data you have recovered but printouts can present problems when you have log files with several and often involves running imaging software overnight and on weekends.
An example of this would be a food industry company acquiring a company in the clothing industry. The computer can be used from the remote place if the suspects computer is connected to other computer or investigators computer using the network. Acquisitions are typically made in order to take control of and build on the target companys strengths and capture synergies MA Synergies MA Synergies occur when the value of a merged company is higher than the sum of the two individual companies.
This is when a company acquires a company in a completely different kind of business industry or sector. Corporate Development focuses on acquisitions that help Cisco capture these market transitions. Cisco segments acquisitions into three categories.
Live hot sparse static physical Courts consider evidence data in. Market acceleration market expansion. Live hot sparse static physical Courts consider evidence data in.
Sometimes a live acquisition is the only way to get data.
Remote Acquisitions With Runtime Software

Guide To Computer Forensics And Investigations Processing Digital Evidence By Nelson Bill Read Imperial Library Of Trantor
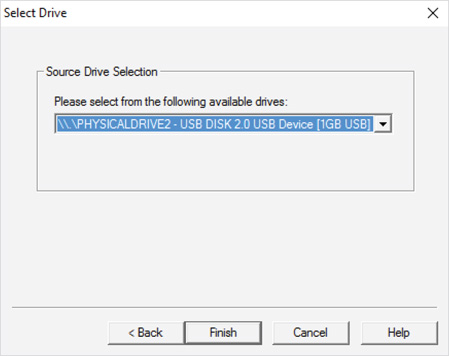
Guide To Computer Forensics And Investigations Processing Digital Evidence By Nelson Bill Read Imperial Library Of Trantor
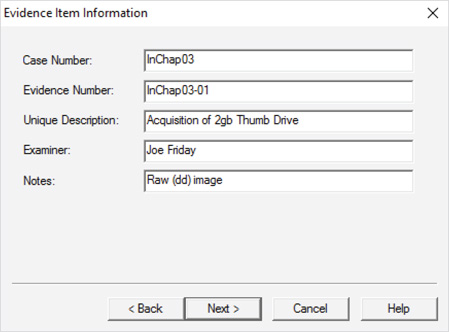
Guide To Computer Forensics And Investigations Processing Digital Evidence By Nelson Bill Read Imperial Library Of Trantor
0 Comments